Malicious actors are moving heaven and earth to perpetuate and amplify their cyberattacks. They are targeting organizations, irrespective of the business size and security posture.
Recently, a hacker tried to cripple a Microsoft customer’s cloud services with the second-largest Distributed Denial-of-Service (DDoS) attack on record.
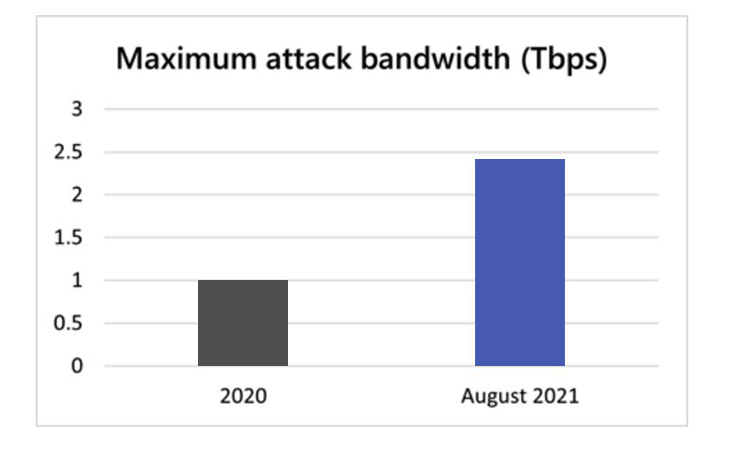
On Monday, the tech giant reported that it encountered a 2.4 Tbps DDOS attack targeting an Azure cloud customer based in Europe in the last week of August. This is next to the 2.5 Tbps DDoS assault Google staved off in 2017.
“This is 140 percent higher than 2020’s 1 Tbps attack and higher than any network volumetric event previously detected on Azure,” said Microsoft.
A DDoS attack is a malicious attempt to bog down a server or network by overwhelming it with a flood of internet traffic. Hackers utilize botnets or a conglomeration of compromised computer systems to generate the attack traffic.
In this case, the attack traffic was generated from around 70,000 sources, particularly from Asia-Pacific countries, such as China, Japan, Vietnam, Malaysia, and Taiwan, as well as from the USA.
Also Read: Microsoft Clinches Prestigious Title in Magic Quadrant Survey
According to Microsoft, the attack vector exploited by the hacker was UDP reflection, which spanned for over 10 minutes. The attack featured very short-lived bursts, each increasing to terabit volumes within seconds.
“In total, we monitored three main peaks, the first at 2.4 Tbps, the second at 0.55 Tbps, and the third at 1.7 Tbps,” reported the Redmond-based tech company.

How Microsoft Mitigated the DDoS Attack?
Though the malicious actors tried to flood an Azure customer with enormous traffic volumes, Microsoft fended off the DDoS attack with ease. All thanks to Azure’s massive scale DDoS protection platform.
Azure’s robust DDoS protection platform is built on distributed DDoS detection and mitigation pipelines. It can effectively scale to absorb tens of terabits of DDoS threats, offering much-needed protection for cloud customers.
The control plane logic orchestrates the attack mitigation lifecycle to dynamically allocate mitigation resources to the locations near the attack sources.
Also Read: Microsoft Trumps Earnings Estimates With Azure’s 51% Growth Rate
In the 2.4 Tbps DDoS attack, the attack traffic was originated in the Asia-pacific region and the US. With Azure’s DDoS mitigation, the attack traffic did not reach the customer region but was instead mitigated at the source locations.
Thanks to Azure’s DDoS mitigation logic, the customer did not suffer any downtime or impact. If the customer had been operating in their own data center instead of relying on Azure, they would have incurred massive financial damage, alongside any intangible expenses.
How Can Effiniti Help You Protect Your Workloads From DDoS Attacks?
Cybercriminals, now more than ever, are continuously adopting new attack vectors to perpetuate invincible cyberattacks. Therefore, organizations must pay utmost attention to develop a robust DDoS response strategy to secure their workloads on Azure cloud.
However, developing and deploying a strong DDoS mitigation strategy that adapts with the evolving attack trends can be a herculean task. Thanks to Azure experts like Effiniti who can help you hammer out a strategic DDoS response plan.
Our Azure experts will empower you to attain Azure DDoS Protection Standard. Besides providing timely mitigation against DDoS attacks, the Azure DDoS Standard will help you realize cost protection. Azure customers will receive data-transfer and application scale-out service credit for resource expenses due to documented DDoS attacks. Such cost protection is indispensable during large attacks that may inflict significant financial damage.
More News Articles: